Office365 Executive Email Hacks Net Millions For Cybercriminal, Federal Investigation Reveals

Table of Contents
Sophisticated Phishing Techniques Employed in the Office365 Hacks
The Office365 executive email hacks uncovered in the federal investigation relied on highly sophisticated phishing techniques. Cybercriminals weren't just sending out generic spam emails; they employed targeted attacks known as spear phishing, CEO fraud, and whaling. These methods focused on specific high-value targets within organizations, increasing the likelihood of success.
-
Spear Phishing: Criminals meticulously researched their targets, crafting emails that appeared to come from trusted sources, often mimicking legitimate business communications. These emails contained convincing details and often included attachments or links leading to malicious websites or malware downloads.
-
CEO Fraud (or Business Email Compromise - BEC): This tactic involves impersonating a high-ranking executive to trick employees into transferring funds or revealing sensitive information. The criminals expertly mimicked the CEO's email address or communication style, making their fraudulent requests appear authentic.
-
Whaling: A more advanced form of phishing targeting high-profile individuals, such as CEOs, CFOs, and other senior executives, who often have access to significant financial resources. These attacks leverage extensive research and sophisticated social engineering tactics to maximize their chances of success.
These techniques often bypassed multi-factor authentication (MFA) by exploiting vulnerabilities in Office365 security or employing social engineering tactics to manipulate victims into revealing their credentials. For example, attackers may use compromised credentials obtained through other means to gain initial access, then leverage this access to further compromise accounts and systems within the organization. Exploitation of known software vulnerabilities, before patches were applied, also played a crucial role.
The Impact of the Office365 Hacks on Businesses and Individuals
The consequences of these Office365 hacks extend far beyond the immediate financial losses. Targeted companies experienced significant financial repercussions, often involving millions of dollars stolen through fraudulent wire transfers or embezzlement.
-
Financial Loss: The direct loss of funds is only the beginning. The cost of investigations, legal fees, regulatory fines, and the disruption to business operations can quickly escalate the financial burden.
-
Reputational Damage: Data breaches erode trust with customers, investors, and partners, leading to significant reputational harm and potential loss of business. The negative publicity surrounding a security breach can be incredibly damaging, impacting long-term sustainability.
-
Legal and Regulatory Consequences: Organizations face potential legal action and substantial fines for failing to adequately protect sensitive data. Compliance with regulations like GDPR and CCPA is critical, and non-compliance can result in severe penalties.
-
Employee Morale: The emotional and psychological impact on executive victims is significant. The stress and anxiety resulting from being targeted, the breach of trust, and the potential consequences can have a negative impact on morale and productivity.
The Federal Investigation and Its Findings
The Federal Bureau of Investigation (FBI) led the investigation into these widespread Office365 executive email hacks. Key findings revealed a sophisticated, international criminal network using advanced techniques to target businesses of all sizes. The investigation successfully traced the criminals’ activities across multiple countries, uncovering a vast operation involving hundreds of victims and millions of dollars in stolen funds. Several arrests and indictments have resulted from the ongoing investigation, with potential future legal actions anticipated.
-
Methods Used to Trace Criminals: Investigators used forensic techniques to trace the flow of funds, analyze network traffic, and uncover the communication channels used by the perpetrators.
-
Geographic Location: The investigation revealed a geographically dispersed criminal network operating across multiple countries, highlighting the global nature of this cybercrime threat.
-
Number of Victims: The investigation encompassed a wide range of victims, from small businesses to large corporations, illustrating the broad reach of these targeted attacks.
Best Practices for Preventing Office365 Executive Email Hacks
Preventing Office365 executive email hacks requires a multi-layered approach to cybersecurity. Robust security measures are essential to mitigate the risk of such attacks. Organizations must prioritize proactive strategies to strengthen their defenses.
-
Multi-Factor Authentication (MFA): Implementing MFA adds an extra layer of security, requiring multiple forms of authentication to access accounts, making it significantly harder for attackers to gain unauthorized access.
-
Software Updates and Patches: Regularly updating software and applying security patches is crucial to prevent exploitation of known vulnerabilities. This includes not only Office365 but also all connected systems and applications.
-
Security Awareness Training: Educating employees about phishing techniques, social engineering tactics, and the importance of secure email practices is vital. Regular training sessions can significantly reduce the risk of human error.
-
Email Filtering and Anti-Phishing Tools: Employing advanced email filtering and anti-phishing tools can help identify and block malicious emails before they reach employees' inboxes.
-
Data Loss Prevention (DLP): Implementing DLP measures helps prevent sensitive data from leaving the organization's control, minimizing the impact of a successful breach.
Conclusion: Protecting Your Organization from Office365 Executive Email Hacks
The federal investigation into Office365 executive email hacks highlights the devastating consequences of these cybercrimes. Millions of dollars have been stolen, reputations have been tarnished, and businesses have suffered irreparable damage. Proactive security measures are not merely optional; they are critical for survival in today's threat landscape. Strengthen your Office365 security by implementing the best practices discussed above. Prevent Office365 email hacks by investing in robust security solutions, educating your employees, and staying vigilant against evolving threats. Protect against executive email compromise by taking immediate action to secure your organization's digital assets. Don't wait until it's too late; secure your Office365 accounts today. For additional resources on enhancing your email security, visit [link to relevant resource].

Featured Posts
-
 Us Trade War Canadian Auto Dealers Strategic Response In Five Key Areas
Apr 24, 2025
Us Trade War Canadian Auto Dealers Strategic Response In Five Key Areas
Apr 24, 2025 -
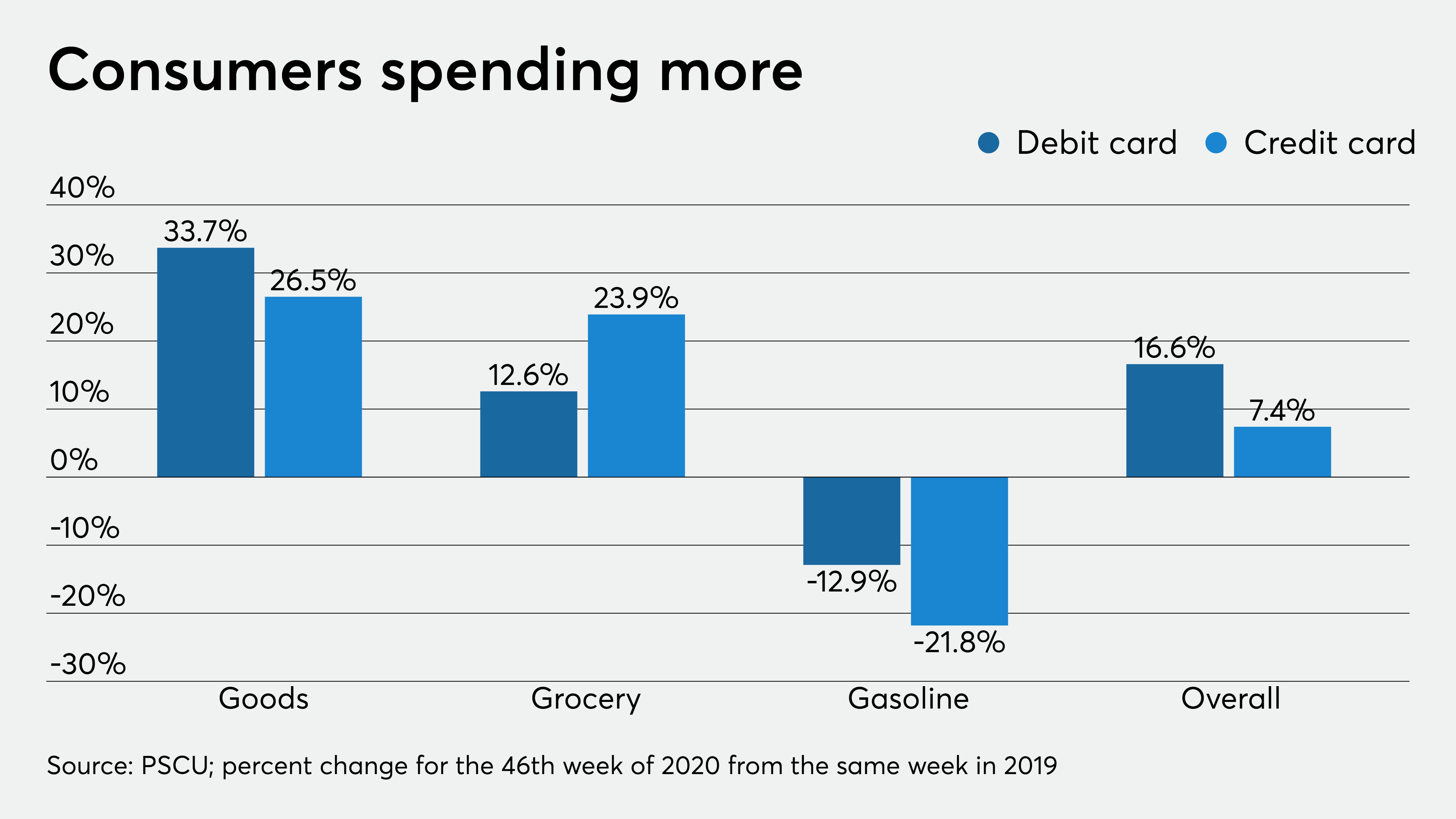 The Impact Of Reduced Nonessential Spending On The Credit Card Industry
Apr 24, 2025
The Impact Of Reduced Nonessential Spending On The Credit Card Industry
Apr 24, 2025 -
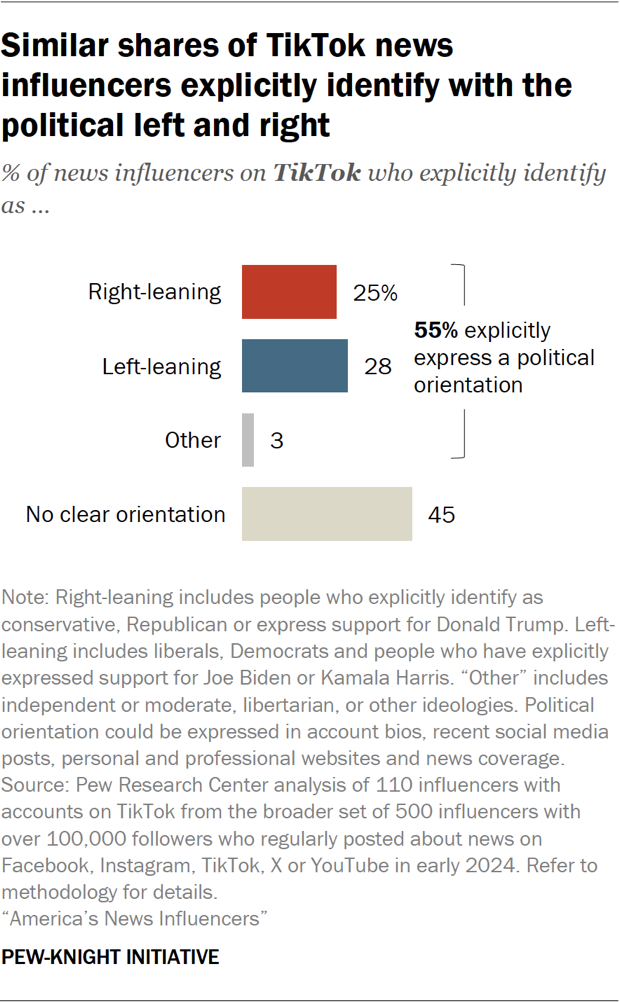 How Instagrams New Video Editor Plans To Disrupt Tik Toks Dominance
Apr 24, 2025
How Instagrams New Video Editor Plans To Disrupt Tik Toks Dominance
Apr 24, 2025 -
 Trumps Transgender Sports Ban Faces Legal Challenge From Minnesota Ag
Apr 24, 2025
Trumps Transgender Sports Ban Faces Legal Challenge From Minnesota Ag
Apr 24, 2025 -
 Reduced Consumer Spending A Challenge For Credit Card Issuers
Apr 24, 2025
Reduced Consumer Spending A Challenge For Credit Card Issuers
Apr 24, 2025
