Massive Office365 Security Failure Costs Executives Millions
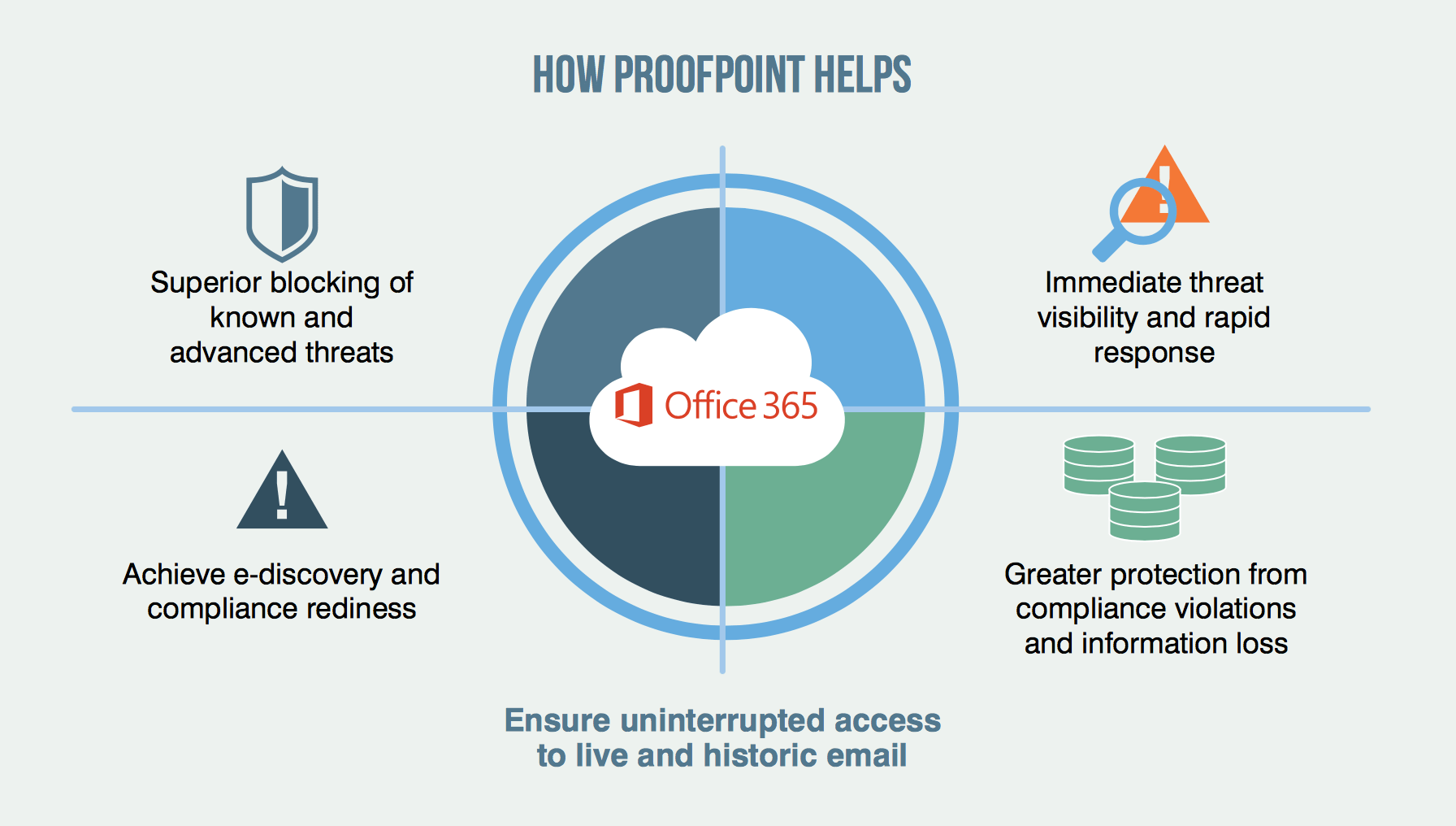
Table of Contents
Phishing and Social Engineering Attacks: A Major Office365 Vulnerability
Phishing and social engineering attacks represent a significant Office365 vulnerability, exploiting human error to gain unauthorized access. These attacks leverage psychological manipulation to trick users into revealing sensitive information or clicking malicious links. The consequences can be catastrophic.
- Examples of common phishing tactics:
- Email spoofing, mimicking legitimate senders like banks or internal colleagues.
- Malicious links disguised as legitimate website URLs.
- Phishing emails containing attachments with malware.
- Consequences of successful phishing attacks:
- Data theft, including sensitive customer information, financial records, and intellectual property.
- Ransomware attacks, encrypting critical data and demanding payment for its release.
- Financial fraud, resulting in significant monetary losses.
- Statistics on the success rate: Studies show that a significant percentage of Office365 users fall victim to phishing attacks annually, highlighting the need for robust email security measures and ongoing employee training. The cost of these Office365 phishing attacks can be crippling.
Weak or Shared Passwords: A Recipe for Disaster
Weak passwords and the practice of password reuse across multiple platforms represent another critical Office365 security vulnerability. These practices make it significantly easier for cybercriminals to gain access to accounts.
- Statistics on weak password breaches: A substantial number of data breaches are attributed to weak or easily guessed passwords.
- Best practices for creating strong, unique passwords: Use a combination of uppercase and lowercase letters, numbers, and symbols; avoid using personal information; and utilize a password manager to generate and store complex passwords securely.
- The importance of multi-factor authentication (MFA): MFA adds an extra layer of security, requiring users to verify their identity through a second factor, such as a code sent to their phone or a biometric scan. This significantly reduces the risk of unauthorized access even if a password is compromised. Implementing robust Office365 password management is paramount.
Lack of Employee Training and Awareness: A Critical Oversight
Insufficient cybersecurity awareness training leaves organizations vulnerable to a wide range of threats. Employees often unknowingly become entry points for cyberattacks.
- Common employee mistakes: Clicking malicious links, downloading infected attachments, sharing sensitive information via insecure channels, and falling for social engineering tactics.
- Benefits of comprehensive cybersecurity awareness programs: Regular training significantly reduces the likelihood of successful phishing attacks and other socially engineered exploits. Employees become more aware of potential threats and understand how to report suspicious activity.
- Methods for effective training: Utilize interactive modules, simulations, and regular phishing campaigns to test employee awareness and reinforce best practices for Office365 security.
Insufficient Security Measures and Misconfigurations
Inadequate security measures and misconfigurations within the Office365 environment can create significant vulnerabilities.
- Examples of common misconfigurations: Improperly configured access controls allowing unauthorized users access to sensitive data; outdated software with known vulnerabilities; and failure to implement necessary security updates.
- Importance of regular security audits and vulnerability assessments: Regular audits identify potential weaknesses and misconfigurations before they can be exploited. Vulnerability assessments pinpoint specific security flaws that need to be addressed.
- The role of a robust SIEM system: A Security Information and Event Management (SIEM) system provides real-time monitoring and analysis of security logs, enabling the detection and response to security incidents. This is crucial for effective Office365 security configuration.
The High Cost of Inaction: Financial Ramifications of Office365 Security Failures
The financial consequences of Office365 security breaches can be devastating.
- Direct costs: Recovery costs (restoring data, repairing systems), legal fees (responding to regulatory investigations), and fines (from regulatory bodies).
- Indirect costs: Reputational damage (loss of customer trust), loss of customers (due to data breaches), decreased productivity (downtime and recovery efforts), and the cost of cybersecurity insurance claims.
- Real-world examples: Numerous high-profile cases demonstrate the significant financial impact of Office365 security failures, with some organizations losing millions due to data breaches and ransomware attacks.
Conclusion: Protecting Your Business from Massive Office365 Security Failures
This article highlighted the significant financial risks associated with common Office365 security vulnerabilities. Phishing, weak passwords, inadequate employee training, and insufficient security measures can lead to costly data breaches, ransomware attacks, and reputational damage. Proactive security measures are crucial. Invest in robust Office365 security solutions, including multi-factor authentication, regular security assessments, comprehensive employee cybersecurity awareness training, and a robust SIEM system. Don't let a massive Office365 security failure cost your business millions. Invest in comprehensive security solutions today! Secure your Office365 environment and protect your business.

Featured Posts
-
 Bfm Bourse Informations Cles Du Marche Du 17 Fevrier A 15h Et 16h
Apr 23, 2025
Bfm Bourse Informations Cles Du Marche Du 17 Fevrier A 15h Et 16h
Apr 23, 2025 -
 Ankara 10 Mart 2025 Pazartesi Iftar Ve Sahur Saatleri
Apr 23, 2025
Ankara 10 Mart 2025 Pazartesi Iftar Ve Sahur Saatleri
Apr 23, 2025 -
 Pazartesi Dizileri 17 Subat Tv Programi
Apr 23, 2025
Pazartesi Dizileri 17 Subat Tv Programi
Apr 23, 2025 -
 Toute L Actualite Boursiere Du Lundi 24 Fevrier Sur Bfm Bourse
Apr 23, 2025
Toute L Actualite Boursiere Du Lundi 24 Fevrier Sur Bfm Bourse
Apr 23, 2025 -
 Private Credit Investment Made Easy Invesco And Barings New Offering
Apr 23, 2025
Private Credit Investment Made Easy Invesco And Barings New Offering
Apr 23, 2025
